2. AWS TGW Reference Architectures for Multi-VPC - 2/5 - Inbound Traffic
Inbound traffic originates outside the VPC, such as the Internet, and is destined to applications or services hosted within your VPCs, such as web servers.
The architecture will share 5 topics:
1. AWS TGW Reference Architectures for Multi-VPC - 1/5 - Brief
2. AWS TGW Reference Architectures for Multi-VPC - 2/5 - Inbound Traffic
3. AWS TGW Reference Architectures for Multi-VPC - 3/5 - Outbound Traffic
4. AWS TGW Reference Architectures for Multi-VPC - 4/5 - East-West Traffic
5. AWS TGW Reference Architectures for Multi-VPC - 5/5 - Backhaul to On-Premises Traffic
All Topology_v20211003(Need to wait for 30 sec to open the 5 web pages)
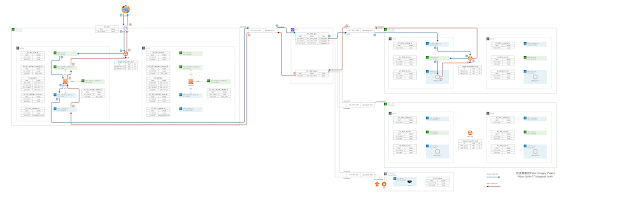
==========Inbound Traffic Flow==========
1. The URL request from the Internet end-user is directed toward example.alb.aws.com.
This request is sent to a DNS. DNS returns an IP address for each of the load balancer’s enabled availability zones.
The client OS picks an IP address and sends the traffic.
Source IP(SIP), Destination IP(DIP), Destination Port (DP)
(SIP: 1.1.1.1, DIP: SEC_ALB Public IP(FQDN_example.alb.aws.com), DP:443)
2. In the SEC VPC, the IGW translates the public destination IP address(SEC_ALB) to the IP address of the Application Load Balancer(SEC_ALB) (10.1.10.x/28 or 10.1.10.1x/28).
In the VPC_SEC Main route table (RT_SEC), the DIP's (SEC_ALB) next hop is local. So traffic will send to SEC_ALB
(SIP: 1.1.1.1, DIP: SEC_ALB network interface 10.1.10.x/28, DP: 443)
3. When traffic into SEC_ALB, SEC_ALB will do health check. NGFW-1 is healthy, traffic will send to NGFW-1.
When ALB setup the Target Groups by IP address with TCP or TLS:
The ALB will change the SIP to ALB network interface IP.
The ALB will use the Target Groups IP to rewrite the DIP.
The ALB will use the Target Groups port to rewrite the DP
The source IP will change to SEC_ALB interface IP (10.1.10.x/28 or 10.1.10.1x/28)
SEC_ALB will translates the DIP to Target group IP (eni-NGFW-1-Eth1/1: 10.1.1.x/24).
(SIP: SEC_ALB network interface 10.1.10.x/28, DIP: eni-NGFW-1-Eth1/1 10.1.1.x/24, DP: 443)
4. After SEC_ALB change the SIP and DIP. Next step is check the route table(RT_SEC_ALB-1a)
In SEC_ALB subnet route table (RT_SEC_ALB-1a), the DIP next hop is the 10.1.0.0/16 local. So traffic will direct send to NGFW-1 untrust Interface.
(SIP: SEC_ALB network interface 10.1.10.x/28, DIP: eni-NGFW-1-Eth1/1 10.1.1.x/24, DP: 443)
5. When NGFW-1 get the traffic from interface Eth1/1, FW will do security profile filtering.
After filtering, NGFW-1 will do Source NAT(SNAT) and destination NAT(DNAT).
Without no SNAT, it is possible to have asymmetric traffic flowing through different NGFWs, which the FWs drop.
Source IP will be translate to NGFW-1 Trust interface IP address (Eth1/2: 10.1.3.x/24)
Destination IP will be translate to FQDN_WEB_ALB network interface IP (10.2.10.x/28 or 10.2.10.1x/28).
In the NGFW-1 route table (RT_NGFW-1), destination IP match the route 10.0.0.0/8 and next hop is the GW IP (10.1.3.1/24) of Trust subnet (SEC_NGFW-1_Trust-1a).
So, traffic will send to the SEC_NGFW-1_Trust-1a.
(SIP: NGFW-1_Eth1/2 10.1.3.x/24, DIP: WEB_ALB network interface 10.2.10.x/28, DP: 443)
6. When traffic into SEC_NGFW-1_Trust-1a, the route table will point out the next hop is TGW.
The VPC_SEC has an attachment (ATT_VPC_SEC). Traffic will use this ATT_VPC_SEC into TGW.
(SIP: NGFW-1_Eth1/2 10.1.3.x/24, DIP: WEB_ALB network interface 10.2.10.x/28, DP: 443)
7. This ATT_VPC_SEC associates with a TGW route table (RT_TGW_SEC).
So traffic next hop will check the RT_TGW_SEC.
(SIP: NGFW-1_Eth1/2 10.1.3.x/24, DIP: WEB_ALB network interface 10.2.10.x/28, DP: 443)
8.In this RT_TGW_SEC route table, there are three routes redistribute(propagation) into this route table.
The VPC_WEB, VPC_APP and On-Premise use propagation redistribute 10.2.0.0/16, 10.3.0.0/61 and 172.16.0.0/16 into the RT_TGW_SEC.
So traffic will know the next hop is the ATT_VPC_WEB.
(SIP: NGFW-1_Eth1/2 10.1.3.x/24, DIP: WEB_ALB network interface 10.2.10.x/28, DP: 443)
9. When traffic reach the ATT_VPC_WEB, this attachment uses VPC attachment connect to VPC_WEB.
There are two subnets associate with this ATT_VPC_WEB. WEB_Landing-1a (10.2.255.0/28) and WEB_Landing-1b (10.2.255.16/28)
Due to the traffic is coming from AZ-1a, so traffic will go to WEB_Landing-1a (10.2.255.0/28) subnet.
(SIP: NGFW-1_Eth1/2 10.1.3.x/24, DIP: WEB_ALB network interface 10.2.10.x/28, DP: 443)
10. When traffic into WEB_Landing-1a (10.2.255.0/28) subnet, the route table (RT_WEB_Landing-1a) will check next hop.
The next hop is the 10.2.0.0/16 local. So traffic will send to WEB_ALB.
(SIP: NGFW-1_Eth1/2 10.1.3.x/24, DIP: WEB_ALB network interface 10.2.10.x/28, DP: 443)
11. When traffic into WEB_ALB, WEB_ALB will do health check. WEB_EC2-1 is healthy, traffic will send to WEB_EC2-1.
When ALB setup the Target Groups by IP address with TCP or TLS:
The ALB will change the SIP to ALB network interface IP.
The ALB will use the Target Groups IP to rewrite the DIP.
The ALB will use the Target Groups port to rewrite the DP
WEB_ALB will translates the DIP to Target group instance (WEB_EC2-1: 10.2.1.x/24).
(SIP: WEB_ALB network interface 10.2.10.x/28, DIP: WEB_EC2-1 10.2.1.x/24, DP: 443)
12. After WEB_ALB change the SIP and DIP. Next step is checking the route table(RT_WEB_ALB-1a)
Next hop is 10.2.0.0/16 local. so traffic will direct send to WEB_EC2-1
(SIP: WEB_ALB network interface 10.2.10.x/28, DIP: WEB_EC2-1 10.2.1.x/24, DP: 443)
==========Return Traffic Flow==========
1. In the WEB VPC, the instance (WEB_EC2-1) sends return traffic back to the WEB_ALB.
In the route table (RT_WEB_EC2-1a), use 10.2.0.0/16 next hop is Local.
Traffic will sent to WEB_ALB.
(SIP: WEB_EC2-1 10.2.1.x/24, Source Port(SP): 443, DIP: WEB_ALB network interface 10.2.10.x/28)
2. When WEB_ALB receives the return traffic, WEB_ALB will change back the source IP and destination IP.
The source IP will change back to WEB_ALB network interface 10.2.10.x/28
The destination IP will change back to NGFW-1_Eth1/2 10.1.3.x/24
The route table will use 0.0.0.0/0, next hop is TGW. So traffic will send to TGW attachment (ATT_VPC_WEB).
(SIP: WEB_ALB network interface 10.2.10.x/28, SP: 443, DIP: NGFW-1_Eth1/2 10.1.3.x/24)
3. This TGW attachment (ATT_VPC_WEB) associates with a TGW route table (RT_TGW_Spoke).
So traffic next hop will check the RT_TGW_Spoke.
(SIP: WEB_ALB network interface 10.2.10.x/28, SP: 443, DIP: NGFW-1_Eth1/2 10.1.3.x/24)
4. In this RT_TGW_Spoke route table, there is only one static default route (0.0.0.0/0) and point to ATT_VPC_SEC.
So traffic will know the next hop is the ATT_VPC_SEC.
(SIP: WEB_ALB network interface 10.2.10.x/28, SP: 443, DIP: NGFW-1_Eth1/2 10.1.3.x/24)
5. When traffic reach the ATT_VPC_SEC, this attachment uses VPC attachment connect to VPC_SEC.
There are two subnets associate with this ATT_VPC_SEC. SEC_Landing-1a (10.1.255.0/28) and SEC_Landing-1b (10.1.255.16/28)
Due to the traffic is coming from AZ-1a, so traffic will go to SEC_Landing-1a (10.1.255.0/28) subnet.
(SIP: WEB_ALB network interface 10.2.10.x/28, SP: 443, DIP: NGFW-1_Eth1/2 10.1.3.x/24)
6. When traffic into subnet (SEC_Landing-1a (10.1.255.0/28)), the route table (RT_SEC_Landing-1a) will check next hop.
The next hop is the 10.1.0.0/16 local. So traffic will send to NGFW-1 Eth1/2 interface.
(SIP: WEB_ALB network interface 10.2.10.x/28, SP: 443, DIP: NGFW-1_Eth1/2 10.1.3.x/24)
7. When NGFW-1 receives the traffic from interface Eth1/2.
According to the session ID, NGFW will know this is a return traffic.
NGFW-1 will do Source NAT(SNAT) and destination NAT(DNAT).
Source IP will be translate back to NGFW-1 Untrust interface IP address (Eth1/1: 10.1.1.x/24)
Destination IP will be translate back to FQDN_SEC_ALB network interface IP (10.1.10.0/28 or 10.1.10.1x/28).
In the NGFW-1 route table (RT_NGFW-1), destination IP match the route 10.1.10.0/24, the next hop is the GW IP (10.1.1.1/24) of Untrust subnet (SEC_NGFW-1_Untrust-1a).
So, traffic will send to the subnet (SEC_NGFW-1_Untrust-1a).
(SIP: eni-NGFW-1-Eth1/1 10.1.1.x/24, SP: 443, DIP: SEC_ALB network interface IP 10.1.10.x/28)
8. When traffic into subnet (SEC_NGFW-1_Untrust-1a (10.1.1.0/24)), the route table (RT_SEC_NGFW-1_Untrust-1a) will check next hop.
The destination IP match 10.1.0.0/16. So next hop is the local. The traffic will direct send to SEC_ALB.
(SIP: eni-NGFW-1-Eth1/1 10.1.1.x/24, SP: 443, DIP: SEC_ALB network interface IP 10.1.10.x/28)
9. When SEC_ALB receives the return traffic, SEC_ALB will change the source IP and destination IP.
The source IP will change back to SEC_ALB public IP (FQDN_example.alb.aws.com)
The destination IP will change back to client public IP (1.1.1.1))
Use IGW send back to the Internet client.
(SIP: SEC_ALB public IP (FQDN_example.alb.aws.com), SP: 443, DIP: 1.1.1.1)
10. IGW send return traffic back to client.
(SIP: SEC_ALB public IP (FQDN_example.alb.aws.com), SP: 443, DIP: 1.1.1.1)
Reference:
1. AWS TGW Reference Architectures for Multi-VPC - 1/5 - Brief
2. AWS TGW Reference Architectures for Multi-VPC - 2/5 - Inbound Traffic
3. AWS TGW Reference Architectures for Multi-VPC - 3/5 - Outbound Traffic
4. AWS TGW Reference Architectures for Multi-VPC - 4/5 - East-West Traffic
5. AWS TGW Reference Architectures for Multi-VPC - 5/5 - Backhaul to On-Premises Traffic
最初發表 / 最後更新: 2021.09.02 / 2021.10.03



0 comments:
Post a Comment