Lab3-10.net file for Dynamips:
##################################################
#
# CCNP Version 5.0: Implementing Secure Converged Wide-Area Networks
# Lab 3.10 Configuring Easy VPN with the IOS CLI
# By Happy Peter http://blog.xuite.net/juilin77/happy
#
##################################################
autostart=false
[localhost:7200]
workingdir = /opt/dynamips/dynagen-0.10.1/UTS/CCNP2/Lab3-10/workingconfig
[[3640]]
# Specify 3640 IOS image on Windows here:
# image = C:\Program Files\Dynamips\images\c3640-jk9o3s-mz.123-14.T7.extracted.bin
# Specify 3640 IOS image on Linux here:
image = /opt/dynamips/images/c3640-jk.bin
ram = 128
disk0 = 0
disk1 = 0
# Choose an idlepc value from the below
idlepc = 0x605ac7b8
mmap = true
ghostios = true
confreg = 0x2102
###########################
#
# Define router instances 1
#
###########################
[[Router ISP]]
model = 3640
console = 2001
slot0 = NM-4T
slot1 = NM-1FE-TX
f1/0 = NIO_linux_eth:eth0
[[Router HQ]]
model = 3640
console = 2002
slot0 = NM-4T
s0/0 = ISP s0/0
s0/1 = HQ2 s0/0
[[Router HQ2]]
model = 3640
console = 2003
slot0 = NM-4T
Objective:
‧ Configure EIGRP on a router
‧ Configure Easy VPN Server
‧ Install the Cisco VPN Client to a host
‧ Connect to the VPN using Cisco VPN client
‧ Verify VPN operation
Scenario:
In this lab, you will set up Easy VPN for the International Travel Agency and connect to Headquarters (HQ) using the IOS Command Line Interface (CLI).
Basic Configuration:
enable
configure terminal
!
no ip domain lookup
!
line console 0
logging synchronous
exec-timeout 0 0
!
host *
Step 1: Configure Addressing
ISP:
interface Serial0/0
ip address 192.168.12.1 255.255.255.0
clock rate 64000
no shutdown
!
interface FastEthernet1/0
ip address 192.168.100.214 255.255.255.192
no shutdown
HQ:
interface Loopback0
ip address 172.16.2.1 255.255.255.0
!
interface Serial0/0
ip address 192.168.12.2 255.255.255.0
no shutdown
!
interface Serial0/1
ip address 172.16.23.2 255.255.255.0
clock rate 64000
no shutdown
HQ2:
interface Loopback0
ip address 172.16.3.1 255.255.255.0
!
interface Serial0/0
ip address 172.16.23.3 255.255.255.0
no shutdown
Step 2: Configure EIGRP AS 1
HQ & HQ2:
router eigrp 1
network 172.16.0.0
no auto-summary
Step 3: Configure a Static Default Route
HQ:
ip route 0.0.0.0 0.0.0.0 192.168.12.1
!
router eigrp 1
redistribute static
Step 4: Enable AAA on HQ
HQ will be the Easy VPN Server
HQ:
username cisco password cisco
!
aaa new-model
aaa authentication login default local none
Step 5: Create the IP Pool
HQ:
ip local pool VPNCLIENTS 172.16.2.100 172.16.2.200
Step 6: Configure the Group Authorization
Use the AAA authorization command aaa authorization network name types to configure the VPN group authentication list. This list will authenticate remote users connecting to the VPN using the group set up in their client.
HQ:
aaa authorization network VPNAUTH local
Step 7: Create an IKE Policy and Group
HQ:
crypto isakmp policy 10
authentication pre-share
encryption aes 256
group 2
Since you don’t know specific peers, you cannot statically associate ISAKMP keys with IP addresses or hosts. So, we configure an ISAKMP client group, instead.
HQ:
crypto isakmp client configuration group ciscogroup
key ciscogroup
pool VPNCLIENTS
acl 100
netmask 255.255.255.0
Source networks permitted by the access-list will be sent to the VPN clients and injected into their IP table.
HQ:
access-list 100 permit ip 172.16.0.0 0.0.255.255 any
Step 8: Configure the IPsec Transform Set
HQ:
crypto ipsec transform-set mytrans esp-3des esp-sha-hmac
Step 9: Create a Dynamic Crypto Map
HQ:
crypto dynamic-map mymap 10
set transform-set mytrans
reverse-route
The first of these will make the map respond to VPN requests. The next command associates an AAA group authorization list with the map. The final command creates a regular crypto map using the dynamic one created earlier.
HQ:
crypto map mymap client configuration address respond
crypto map mymap isakmp authorization list VPNAUTH
crypto map mymap 10 ipsec-isakmp dynamic mymap
Finally, apply the crypto map to the interface that is facing ISP
HQ:
interface serial 0/0
crypto map mymap
Step 10: Enable IKE DPD and User Authentication
IKE Dead Peer Detection (DPD) is a keepalive mechanism for checking VPN connections.
Use a keepalive timer of 30 seconds and a retry-time of 5 seconds.
HQ:
crypto isakmp keepalive 30 5
Xauth, or extended authentication, is the method used to authenticate VPN clients on a per-user basis, in addition to the group authentication.
HQ:
aaa authentication login VPNAUTH local
username ciscouser password ciscouser
Globally configure the Xauth timeout to be 60 seconds
HQ:
crypto isakmp xauth timeout 60
Finally, associate the AAA login list with the crypto map configured earlier
HQ:
crypto map mymap client authentication list VPNAUTH
Step 11: Install the Cisco VPN Client
My host is a MS XP OS in VMware.
IP address: 192.168.100.213 /26
Gateway: 192.168.100.214
Host:
Next > Next > .... > Finish
Step 12: Test Access from Client without VPN Connection
Step 13: Connect to the VPN
Step 14: Test Inside VPN Connectivity
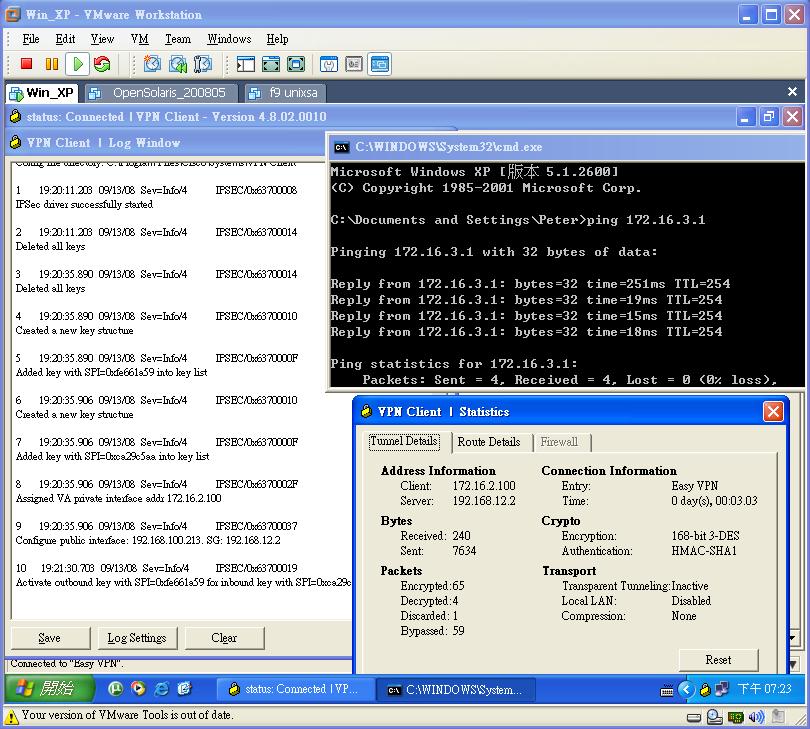
Step 15: Verify VPN Operation using the CLI
HQ:
show crypto isakmp sa
dst src state conn-id slot status
192.168.12.2 192.168.100.213 QM_IDLE 1 0 ACTIVE
Step 16: Disconnecting the VPN Client
Host:
Right-click the padlock icon in the system tray and click "Disconnect". The VPN client will disconnect.
Final Configurations
ISP:
hostname ISP
!
no ip domain lookup
!
interface Serial0/0
ip address 192.168.12.1 255.255.255.0
clock rate 64000
no shutdown
!
interface FastEthernet1/0
ip address 192.168.100.214 255.255.255.192
no shutdown
!
line con 0
exec-timeout 0 0
logging synchronous
!
end
HQ:
hostname HQ
!
aaa new-model
!
aaa authentication login default local none
aaa authentication login VPNAUTH local
aaa authorization network VPNAUTH local
!
no ip domain lookup
!
username cisco password 0 cisco
username ciscouser password 0 ciscouser
!
crypto isakmp policy 10
encr aes 256
authentication pre-share
group 2
crypto isakmp keepalive 30 5
crypto isakmp xauth timeout 60
!
crypto isakmp client configuration group ciscogroup
key ciscogroup
pool VPNCLIENTS
acl 100
netmask 255.255.255.0
!
crypto ipsec transform-set mytrans esp-3des esp-sha-hmac
!
crypto dynamic-map mymap 10
set transform-set mytrans
reverse-route
!
crypto map mymap client authentication list VPNAUTH
crypto map mymap isakmp authorization list VPNAUTH
crypto map mymap client configuration address respond
crypto map mymap 10 ipsec-isakmp dynamic mymap
!
interface Loopback0
ip address 172.16.2.1 255.255.255.0
!
interface Serial0/0
ip address 192.168.12.2 255.255.255.0
crypto map mymap
no shutdown
!
interface Serial0/1
ip address 172.16.23.2 255.255.255.0
clock rate 64000
no shutdown
!
router eigrp 1
redistribute static
network 172.16.0.0
no auto-summary
!
ip local pool VPNCLIENTS 172.16.2.100 172.16.2.200
!
ip route 0.0.0.0 0.0.0.0 192.168.12.1
!
access-list 100 permit ip 172.16.0.0 0.0.255.255 any
!
line con 0
exec-timeout 0 0
logging synchronous
!
end
HQ:
hostname HQ2
!
no ip domain lookup
!
interface Loopback0
ip address 172.16.3.1 255.255.255.0
!
interface Serial0/0
ip address 172.16.23.3 255.255.255.0
no shutdown
!
router eigrp 1
network 172.16.0.0
no auto-summary
!
line con 0
exec-timeout 0 0
logging synchronous
!
end
Reference:
Cisco Networking Academy
http://www.cisco.com/web/learning/netacad/index.html
CCNP Version 5.0: Implementing Secure Converged Wide-Area Networks
Student Lab Manual
最初發表 / 最後更新: 2008.09.29 / 2018.06.11




0 comments:
Post a Comment