Step 1. Changing the wrapper-linux permissions.
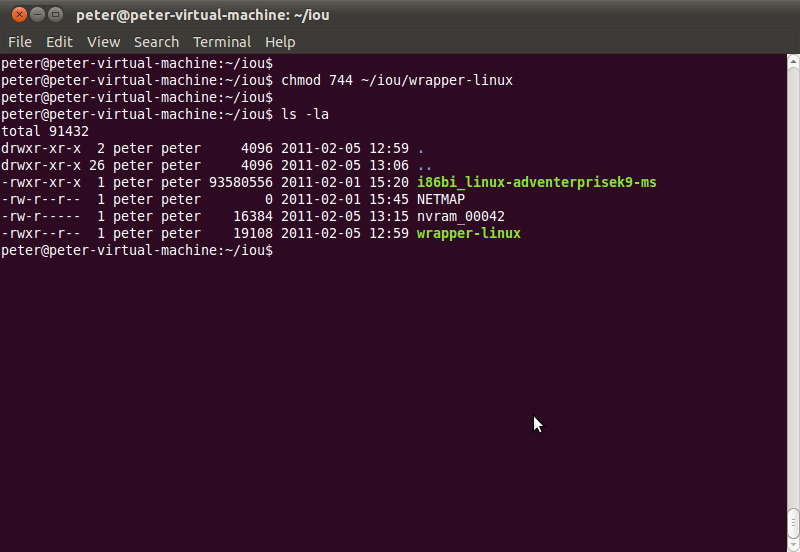
Step 2. Running the wrapper-linux
a. The image file is the i86bi_linux-adventerprisek9-ms (-m ./i86bi_linux-adventerprisek9-ms)
b. Opening the TCP port 2000 for telnet (-p 2000)
c. The router ID is 42 (42)
d. You can run this process on the background (&)
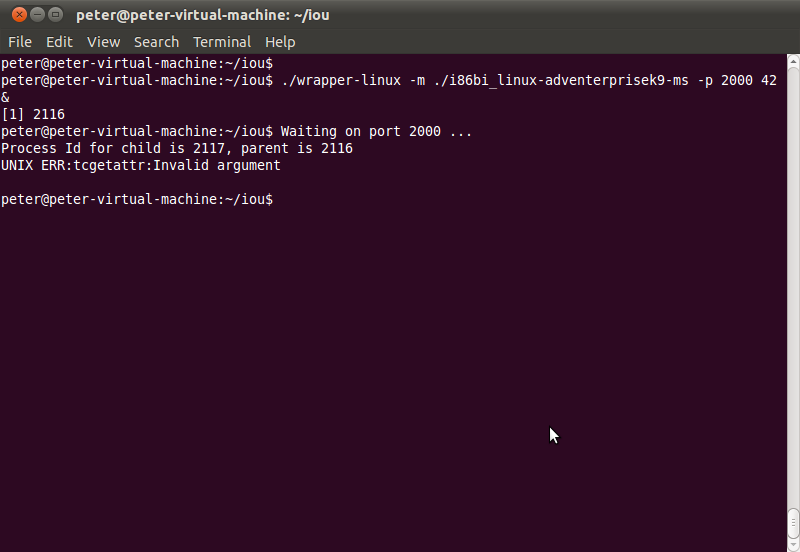
Step 3. Telnet to router and enjoy it \(^3^)/
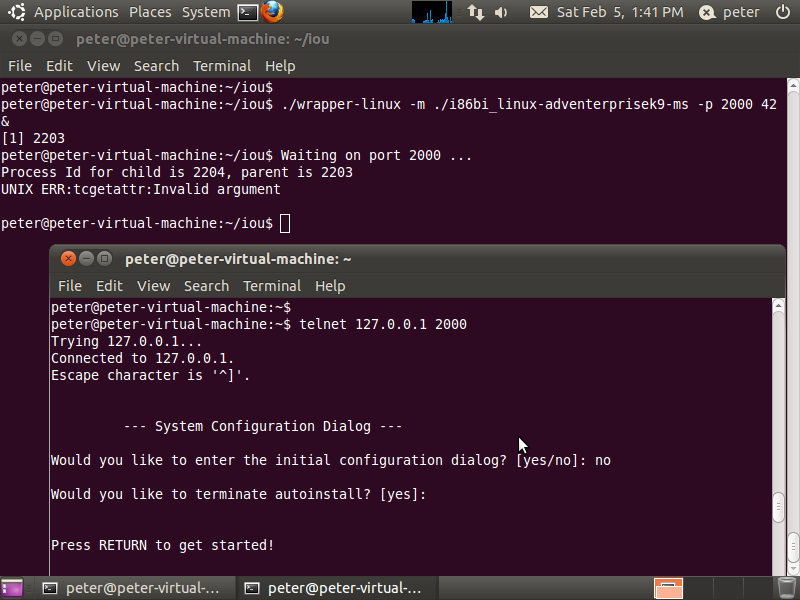
Step 4. Stoping this process
a. Checking this process ($jobs -l)
b. killing this process ($kill -15 %1)
Reference:
evilrouters.net: http://evilrouters.net/
Thanks for "Le****e sir" (真。牛人)
最初發表 / 最後更新: 2011.02.05 / 2018.06.08




0 comments:
Post a Comment