Lab3-5_option.net file for Dynamips:
##################################################
#
# CCNP Version 5.0: Implementing Secure Converged Wide-Area Networks
# Lab 3.5 Configuring Site-to-Site IPsec VPNs with the IOS CLI(Option)
# By Happy Peter http://blog.xuite.net/juilin77/happy
#
##################################################
autostart=false
[localhost:7200]
workingdir = /opt/dynamips/dynagen-0.10.1/UTS/CCNP2/Lab3-5/workingconfig
[[3640]]
# Specify 3640 IOS image on Windows here:
# image = C:\Program Files\Dynamips\images\c3640-jk9o3s-mz.123-14.T7.extracted.bin
# Specify 3640 IOS image on Linux here:
image = /opt/dynamips/images/c3640-jk.bin
ram = 128
disk0 = 0
disk1 = 0
# Choose an idlepc value from the below
idlepc = 0x605ac7b8
mmap = true
ghostios = true
confreg = 0x2102
###########################
#
# Define router instances 1
#
###########################
[[Router R1]]
model = 3640
console = 2001
slot0 = NM-1FE-TX
[[Router R2]]
model = 3640
console = 2002
slot0 = NM-1FE-TX
slot1 = NM-4T
F0/0 = R1 F0/0
S1/0 = R3 S0/0
[[Router R3]]
model = 3640
console = 2003
slot0 = NM-4T
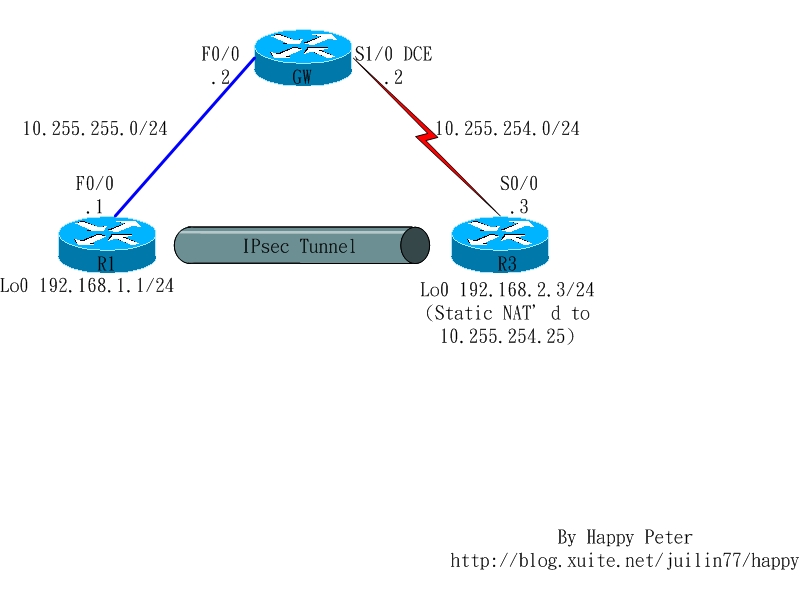
Objective:
GW Router does not know about 192.168.1.0/24 & 192.168.2.0/24. R1 and R3 still can creat Tunnel mode IPSec VPN in NAT mode.
Basic Configuration:
enable
configure terminal
!
no ip domain lookup
!
line console 0
logging synchronous
exec-timeout 0 0
!
host *
Step 1: Configure Addressing
R1:
interface Loopback0
ip address 192.168.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address 10.255.255.1 255.255.255.0
no shutdown
GW:
interface FastEthernet0/0
ip address 10.255.255.2 255.255.255.0
no shutdown
!
interface Serial1/0
ip address 10.255.254.2 255.255.255.0
clock rate 64000
no shutdown
R3:
interface Loopback0
ip address 192.168.2.3 255.255.255.0
!
interface Serial0/0
ip address 10.255.254.3 255.255.255.0
no shutdown
Step 2: Configure default route
R1
ip route 0.0.0.0 0.0.0.0 10.255.255.2
R3:
ip route 0.0.0.0 0.0.0.0 10.255.254.2
!!!Verify!!!
R1#ping 10.255.254.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.255.254.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/12/24 ms
R1#
Step 3: Create IKE Policies
R1 & R3:
crypto isakmp policy 10
authentication pre-share
R1#show crypto isakmp policy
Global IKE policy
Protection suite of priority 10
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1#
Step 4: Configure Pre-Shared Keys
R1:
crypto isakmp key 6 ciscokey address 10.255.254.3
R3:
crypto isakmp key 6 ciscokey address 10.255.255.1
Step 5: Configure the IPsec Transform Set
R1 & R3:
crypto ipsec transform-set 50 ah-sha-hmac esp-aes 256 esp-sha-hmac
Step 6: Define Interesting Traffic
R1:
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
R3:
access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
Step 7: Create and Apply Crypto Maps
R1:
crypto map MYMAP 20 ipsec-isakmp
set peer 10.255.254.3
set security-association lifetime seconds 900
set transform-set 50
set pfs group5
match address 101
!
interface FastEthernet0/0
crypto map MYMAP
R3:
crypto map MYMAP 20 ipsec-isakmp
set peer 10.255.255.1
set security-association lifetime seconds 900
set transform-set 50
set pfs group5
match address 101
!
interface Serial0/0
crypto map MYMAP
Step 8: Set up NAT
R1:
ip nat inside source list 175 interface FastEthernet0/0 overload
!
access-list 175 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 175 permit ip 192.168.1.0 0.0.0.255 any
!
interface Loopback0
ip nat inside
!
interface FastEthernet0/0
ip nat outside
R3:
ip nat inside source list 122 interface Serial0/0 overload
ip nat inside source static 192.168.2.3 10.255.254.25 route-map nonat
!
access-list 122 deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 122 permit ip 192.168.2.0 0.0.0.255 any
access-list 150 deny ip host 192.168.2.3 192.168.1.0 0.0.0.255
access-list 150 permit ip host 192.168.2.3 any
!
route-map nonat permit 10
match ip address 150
!
interface Loopback0
ip nat inside
!
interface Serial0/0
ip nat outside
Step 9: Verify IPsec Configuration
R1 & R3:
#show crypto isakmp policy
Global IKE policy
Protection suite of priority 10
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1 & R3:
#show crypto ipsec transform-set
Transform set 50: { ah-sha-hmac }
will negotiate = { Tunnel, },
{ esp-256-aes esp-sha-hmac }
will negotiate = { Tunnel, },
R1#show crypto map
Crypto Map "MYMAP" 20 ipsec-isakmp
Peer = 10.255.254.3
Extended IP access list 101
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
Current peer: 10.255.254.3
Security association lifetime: 4608000 kilobytes/900 seconds
PFS (Y/N): Y
DH group: group5
Transform sets={
50,
}
Interfaces using crypto map MYMAP:
FastEthernet0/0
R3#show crypto map
Crypto Map "MYMAP" 20 ipsec-isakmp
Peer = 10.255.255.1
Extended IP access list 101
access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
Current peer: 10.255.255.1
Security association lifetime: 4608000 kilobytes/900 seconds
PFS (Y/N): Y
DH group: group5
Transform sets={
50,
}
Interfaces using crypto map MYMAP:
Serial0/0
Interfaces using crypto map myvpn:
Step 10: Verify
R1#ping 192.168.2.3 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.3, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/15/28 ms
R1#show crypto isakmp sa
dst src state conn-id slot status
10.255.254.3 10.255.255.1 QM_IDLE 1 0 ACTIVE
R1#show crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: MYMAP, local addr 10.255.255.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer 10.255.254.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 28, #pkts encrypt: 28, #pkts digest: 28
#pkts decaps: 28, #pkts decrypt: 28, #pkts verify: 28
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 12, #recv errors 0
local crypto endpt.: 10.255.255.1, remote crypto endpt.: 10.255.254.3
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x1C7B7695(477853333)
inbound esp sas:
spi: 0xE721030D(3877700365)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: SW:4, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4563419/322)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
spi: 0x5280982A(1384159274)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: SW:4, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4563419/321)
replay detection support: Y
Status: ACTIVE
inbound pcp sas:
outbound esp sas:
spi: 0x1C7B7695(477853333)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2003, flow_id: SW:3, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4563419/321)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
spi: 0x4DDD15A0(1306334624)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2003, flow_id: SW:3, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4563419/321)
replay detection support: Y
Status: ACTIVE
outbound pcp sas:
Final Configurations
R1:
hostname R1
!
no ip domain lookup
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key 6 ciscokey address 10.255.254.3
!
crypto ipsec transform-set 50 ah-sha-hmac esp-aes 256 esp-sha-hmac
!
crypto map MYMAP 20 ipsec-isakmp
set peer 10.255.254.3
set security-association lifetime seconds 900
set transform-set 50
set pfs group5
match address 101
!
interface Loopback0
ip address 192.168.1.1 255.255.255.0
ip nat inside
!
interface FastEthernet0/0
ip address 10.255.255.1 255.255.255.0
ip nat outside
crypto map MYMAP
no shutdown
!
ip route 0.0.0.0 0.0.0.0 10.255.255.2
!
ip nat inside source list 175 interface FastEthernet0/0 overload
!
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 175 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 175 permit ip 192.168.1.0 0.0.0.255 any
!
line con 0
exec-timeout 0 0
logging synchronous
!
end
GW:
hostname GW
!
no ip domain lookup
!
interface FastEthernet0/0
ip address 10.255.255.2 255.255.255.0
no shutdown
!
interface Serial1/0
ip address 10.255.254.2 255.255.255.0
clock rate 64000
no shutdown
!
line con 0
exec-timeout 0 0
logging synchronous
!
end
R3:
hostname R3
!
no ip domain lookup
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key 6 ciscokey address 10.255.255.1
!
crypto ipsec transform-set 50 ah-sha-hmac esp-aes 256 esp-sha-hmac
!
crypto map MYMAP 20 ipsec-isakmp
set peer 10.255.255.1
set security-association lifetime seconds 900
set transform-set 50
set pfs group5
match address 101
!
interface Loopback0
ip address 192.168.2.3 255.255.255.0
ip nat inside
!
interface Serial0/0
ip address 10.255.254.3 255.255.255.0
ip nat outside
crypto map MYMAP
no shutdown
!
ip route 0.0.0.0 0.0.0.0 10.255.254.2
!
ip nat inside source list 122 interface Serial0/0 overload
ip nat inside source static 192.168.2.3 10.255.254.25 route-map nonat
!
access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 122 deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 122 permit ip 192.168.2.0 0.0.0.255 any
access-list 150 deny ip host 192.168.2.3 192.168.1.0 0.0.0.255
access-list 150 permit ip host 192.168.2.3 any
!
route-map nonat permit 10
match ip address 150
!
line con 0
exec-timeout 0 0
logging synchronous
!
end
Reference:
Cisco Networking Academy
http://www.cisco.com/web/learning/netacad/index.html
Configuring a Router IPsec Tunnel Private-to-Private Network with NAT and a Static
http://www.cisco.com/en/US/tech/tk583/tk372/technologies_configuration_example09186a0080094634.shtml
最初發表 / 最後更新: 2008.09.27 / 2018.06.11



0 comments:
張貼留言